Whoa, things are heating up again in the Android world... Watch out for "Crocodilus," a nasty new banking trojan that's currently zeroing in on folks in Spain and Turkey.  Now, it might sound like your standard-issue malware at first, but this one's got some particularly devious tricks. It's not *just* snagging login details – it's also after the seed phrases for crypto wallets.
Now, it might sound like your standard-issue malware at first, but this one's got some particularly devious tricks. It's not *just* snagging login details – it's also after the seed phrases for crypto wallets. 
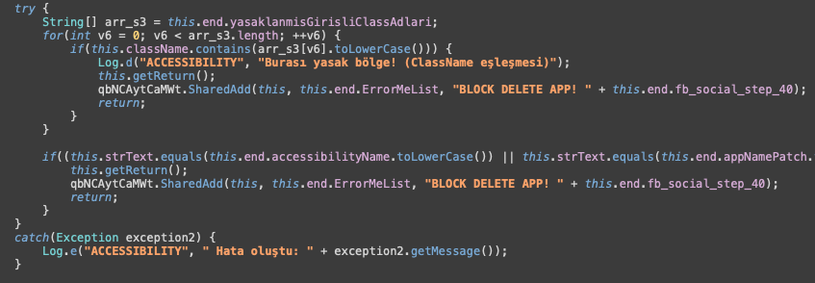
Here’s the kicker: it disguises itself as Google Chrome and tries to trick you into granting Accessibility Services permissions. If you give it that access, you've basically handed over the keys to your device. Seriously, it can then read everything on your screen, see every tap you make... and you wouldn't even know, because it can black out the screen while it does its dirty work.  Total stealth mode.
Total stealth mode.
As someone in penetration testing, I unfortunately run into this kind of threat all too often. Clients sometimes say, "But I have antivirus software!" The hard truth? Against sophisticated attacks like this, basic AV often won't cut it.
So, the usual advice is more critical than ever: Be super careful about the apps you install and *always* double-check the permissions they ask for! And please, use Multi-Factor Authentication (MFA) wherever you can! 
I'm curious – what security measures do you have running on your smartphone? Drop your tips below!