#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #nerdlings #fantasy
Recent searches
Search options
#elf
#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #nerdlings #fantasy
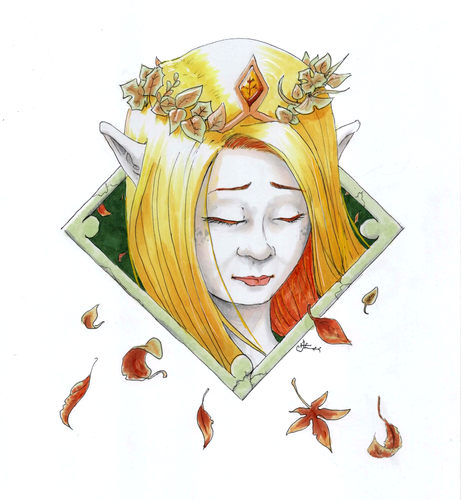
Autumn / Otoño
(Share, save, comment!)
In the southern hemisphere is autumn now, and slowly the leaves left the trees with golden sparks. I love this season!
En el hemisferio sur ya estamos en otoño, y lentamente las hojas abandonan los árboles con chispazos dorados. ¡Me encanta esta estación!
.
.
#elf #ink #copic #markers #traditionalart #noai #fantasy #markersdrawing #drawing #art #mastoart #mastoartist
Operation ForumTroll exploits zero-days in Google Chrome
In March 2025, a sophisticated malware campaign exploited a zero-day vulnerability in Google Chrome to infect targets. The attack, dubbed Operation ForumTroll, used personalized phishing emails with short-lived links to deliver malware. Kaspersky detected the exploit, reported it to Google, and an update was released to fix the vulnerability (CVE-2025-2783). The campaign targeted media outlets, educational institutions, and government organizations in Russia, disguising itself as invitations to the 'Primakov Readings' forum. The attackers' goal appears to be espionage, and the sophistication of the malware suggests a state-sponsored APT group is behind the operation. The exploit chain involved sandbox escape and remote code execution, though only the former was fully analyzed.
Pulse ID: 67e33790837554926530dc06
Pulse Link: https://otx.alienvault.com/pulse/67e33790837554926530dc06
Pulse Author: AlienVault
Created: 2025-03-25 23:09:04
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #nerdlings #fantasy
Loestvaria
Theme for the elf, Loestvaria, from my fantasy album/short story 'Relics of Aeternum: Dragonsoul Chronicle'. For guitar and harp.
➣ Full song: https://youtu.be/qFquIWBkYns
#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #nerdlings #fantasy
#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #nerdlings
The second redraw of one artwork I made when I was 16.
The original concept was supposed to be lighthearted and charming, but due to skill issue it ended up looking silly. This piece matches the vibe I was going for, so I decided not to redraw it anymore, even though I don't like the background that much.
This is the only drawing (so far) where Ferimus is actually wearing pants. (And where Riamidea the Necromancer is holding an umbrella, but not wearing pants is actually weirder)
#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #nerdlings
Bonsoir.
Écoutez Elf.
Ronnie James Dio a 30 ans à la sortie du premier album "Elf" du groupe.
Titres majeurs : Fifth Avenue, I'm Coming Back For You, Love Me Like a Woman.
(Ça mérite un ampli qui va jusqu'à 12.)
(Et Never More )
#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon #wargaming #warhammer40k #miniaturepainting #warhammercommunity #warhammer #wh40k #paintingwarhammer #nerdlings
#paintingwarhammer #warhammercommunity #warhammerfantasy #wargames #wargaming #fantasy #warhammerphotography #warhammer #miniatures #miniaturepainting #chaos #chaoswarriors #skirmishgames #barbarian #dnd #dnd5e #rpg #ttrpg #terrain #elf #elves #highelves #highelf #dungeon
Dragon RaaS | Pro-Russian Hacktivist Group Aims to Build on "The Five Families" Cybercrime Reputation
Dragon RaaS is a ransomware group that emerged in July 2024 as an offshoot of Stormous, part of a larger cybercrime syndicate known as 'The Five Families'. The group markets itself as a sophisticated Ransomware-as-a-Service operation but often conducts defacements and opportunistic attacks rather than large-scale ransomware extortion. Dragon RaaS primarily targets organizations in the US, Israel, UK, France, and Germany, exploiting vulnerabilities in web applications, using brute-force attacks, and leveraging stolen credentials. The group operates two ransomware strains: a Windows-focused encryptor based on StormCry and a PHP webshell. Despite claims of creating a unique ransomware variant, analysis reveals that Dragon RaaS's payloads are slightly modified versions of StormCry.
Pulse ID: 67db2bceaeb33fde1496fef2
Pulse Link: https://otx.alienvault.com/pulse/67db2bceaeb33fde1496fef2
Pulse Author: AlienVault
Created: 2025-03-19 20:40:46
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Berlin was a raw & intense & bare trial of new ideas for the Dystopia Wetlands EP ♪ ♫/ world / its creatures. It’s beautiful to have some time to look back - resonate - appreciate - imagine further.
Thank you all for the support. Gives me warmth.
♪ ♫◉●•◦*.:ₒᵒᴼᵒ
ₒ。.✿`°¤,¸.•*´¯