Amid US privacy concerns under Trump, some EU organizations are considering moving away from AWS, Google Cloud, and Azure. Two European cloud providers report a surge in interest. #EU #CloudComputing #PrivacyConcerns #AWS #GoogleCloud #Azure #TechNews #DataPrivacy
Recent searches
Search options
#dataprivacy
For those #Genealogists who are interested, this video shows you how to copy your 23&Me results to #GedMatch , after you DOWNLOAD them from #23andMe .
#GedMatch has a host of great tools that allow you to continue analyzing your DNA and build your #FamilyTree with #GeneticGenealogy .
Be aware that law enforcement can also use this particular database. However, you must OPT IN to allow your data to be accessible to them. So far, they have been using it to help identify unknown "Jane/John Doe" bodies and solve #ColdCase crimes.
https://youtu.be/Ck9S5poH_tA?si=hN45CqTYDkEboZ9p
@geneadons #Geneadons #Genealogy #dnatestingfirmintrouble #DNAtesting #DataPrivacy #DNAdata #DNAdatabases #23andMeBankruptcy
How to delete your 23andMe data and why you should do it now
https://www.zdnet.com/article/how-to-delete-your-23andme-data-and-why-you-should-do-it-now/ #23andMe #Privacy #DataPrivacy #Tech #Security #GeneticTesting

EUROPE
EU Firms Shift from US Cloud Providers
Rising concerns push EU firms toward European cloud services.
Swiss Exoscale & Swedish Elastx report increased demand from businesses seeking alternatives.
EU-US data-sharing uncertainty drives privacy concerns.
Mobile AI Agents Security Risks
Mobile AI agents can significantly compromise security and privacy due to their extensive access requirements and reliance on cloud processing. When performing tasks such as booking concerts or managing schedules, these agents need access to sensitive information like credit card details, calendar entries, your contacts and messaging apps, which can expose users to risks if the data falls into the wrong hands. (Reminder that email, contacts and calanders are not encrypted).
Moreover, integrating AI agents with applications like messaging services can undermine end-to-end encryption, as data must often be sent to cloud servers for processing and then returned to the device This process can leave user data vulnerable to interception or misuse.
Additionally, some mobile AI apps, like DeepSeek, have been flagged for poor security practices, including the use of hard-coded encryption keys and the transmission of unencrypted user and device data to external entities These issues highlight the broader security and privacy concerns associated with mobile AI agents.
Experts like Meredith Whittaker CEO of the Signal App, have warned that the integration of AI agents poses a "profound issue" with security and privacy, potentially breaking the "blood-brain barrier" between application layers and the operating system, thereby muddying data and increasing vulnerabilities. #encryption #aiagent #dataprotection #dataprivacy #signal
23andMe's bankruptcy has customers worried about the privacy of their genetic data @Engadget lays out the steps you can take to delete your records from the site. #23andMe #DataPrivacy #Tech #Technology https://flip.it/nRPW24

Welp, it’s time to add to my ongoing list of things currently occurring in the US federal government that would get me, a privacy practitioner, immediately fired if I did them:
New:
-Using non-approved apps to transmit sensitive information
-sending sensitive information without double-checking recipient list
-setting records to auto-delete in contravention of records retention policy
Previously:
-Connecting an unknown external server to the network
-data access without background check
-ignoring least necessary access principles
-admin access without any controls
-improper segmentation/separation of duties
-coding directly on prod
-data to 3rd party tools without due diligence
-Delete security documentation because it contains “forbidden words” used in other contexts
The EU is preparing to fine Meta up to $1 billion for violating the Digital Markets Act with its ‘pay or consent’ model for Facebook/Instagram
#Meta #Facebook #Instagram #DigitalMarketsAct #BigTech #Antitrust #DataPrivacy #EURegulation #AdTech #Europe
https://winbuzzer.com/2025/03/25/meta-faces-1-billion-eu-fine-over-pay-or-consent-model-xcxwbn/
Experts from Ecommpay, Deloitte Malta, FINOM, and Scytale will discuss compliance strategies for startups at the EU-Startups Summit 2025 in Malta.The EU-Startups Summit 2025, set for April 24-25 in Malta, will feature a panel of experts from Ecommpay, Deloitte Malta, FINOM, and Scytale. #dataprivacy #EUAIAct #fintech #gdpr #startups #redrobot
Hey folks, ready for your daily dose of cyber intel? ️
Tuesday's update is out and it's packed with need-to-know updates:
Critical Next.js Flaw: Authorization bypass vulnerability (CVE-2025-29927) impacting versions before 15.2.3. Upgrade ASAP or block those 'x-middleware-subrequest' headers!
Weaver Ant's Long Game: Chinese hackers spied on a telco network for four years using compromised Zyxel routers and custom web shells. Talk about persistence!
VanHelsing RaaS Emerges: A new ransomware player targeting Windows, ARM, ESXi systems. Keep an eye on this one!
Oracle Cloud Breach Claims: Did they or didn't they? Oracle denies a breach, but a threat actor is claiming otherwise.
Ukrainian Railway Hit: Cyberattack disrupts online ticket sales amidst crucial transport operations. Resilience is key.
DrayTek Router Chaos: ISPs are scrambling as DrayTek routers enter reboot loops. Potential vulnerability or buggy update at play.
AI-Enhanced Cybercrime: Europol warns that organized crime is leveling up with AI, partnering with state-aligned entities.
Starlink Intercepted: Thai authorities seize Starlink transmitters headed for Myanmar scam centers. Criminals are finding ways around cut-offs.
Cybercrime Crackdown: 300+ suspects arrested in Africa for cyber scams. A win for international law enforcement!
23andMe's Bankruptcy Woes: Privacy advocates raise concerns about DNA data as 23andMe files for bankruptcy. What happens to all that genetic info?
Pennsylvania County Ransomware: Sensitive data stolen during a ransomware attack. Another reminder to shore up those defenses.
China Bans Facial Recognition: Consent is now required for facial recognition in China. But are there exceptions for government and AI training?
Dive into the full details here: https://opalsec.io/daily-news-update-tuesday-march-25-2025-australia-melbourne/
Stay vigilant, stay informed, and let's keep the digital world a little safer, one update at a time.

TikTok’s Fate in the U.S. Hangs in the Balance: Will ByteDance Sell or Face a Ban?
#TikTokBan #ByteDance #USPolitics #SocialMedia #TechNews #NationalSecurity #DataPrivacy #Oracle #TikTokUS #BreakingNews #DigitalSecurity #SenateDebate #TechPolicy
https://www.techi.com/senators-urge-trump-delay-tiktok-sale-deadline/

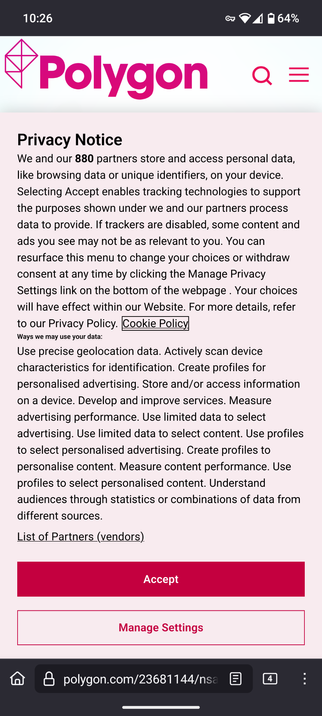
Holy shit Polygon, 880 partners?!
Notice there's no reject button.
---
Privacy Notice
We and our 880 partners store and access personal data, like browsing data or unique identifiers, on your device.
Ways we may use your data:
Use precise geolocation data. Actively scan device characteristics for identification. Create profiles for personalised advertising. Store and/or access information on a device. Develop and improve services. Measure advertising performance. Use limited data to select advertising. Use limited data to select content. Use profiles to select personalised advertising. Create profiles to personalise content. Measure content performance. Use profiles to select personalised content. Understand audiences through statistics or combinations of data from different sources.
China has introduced new rules banning facial recognition without consent in private spaces, like hotel rooms, effective last Friday. #China #FacialRecognition #Privacy #TechRegulation #DataPrivacy #AI #Security #NewLaws
I wrote about how the US military invented the dark web #tech #politics #futurist #technologist #dataprivacy https://www.derekguzman.com/the-cia-invented-the-dark-web/
I wrote about how the US military invented the dark web #tech #politics #futurist #technologist #dataprivacy https://derekguzman.ghost.io/ghost/#/editor/post/67e0a73105272400010a2725
23andMe's Bankruptcy: A Data Privacy Crisis in Genetic Testing
As 23andMe files for Chapter 11 bankruptcy, the future of its vast genetic data trove hangs in the balance. With privacy advocates raising alarms, customers are urged to take action to protect their p...
https://news.lavx.hu/article/23andme-s-bankruptcy-a-data-privacy-crisis-in-genetic-testing
23andMe's Bankruptcy: A Wake-Up Call for Data Privacy in Genetic Testing
As 23andMe files for Chapter 11 bankruptcy, the tech community is on high alert regarding the security of sensitive genetic data. With privacy experts raising concerns, customers are urged to delete t...
https://news.lavx.hu/article/23andme-s-bankruptcy-a-wake-up-call-for-data-privacy-in-genetic-testing
It's official...
23&Me has filed for bankruptcy.
The company has been rejecting any buyout attempts, but their Board of Directors is now saying that a Court-supervised sale is the best path forward. Part of the reason for their financial troubles was a 2023 #DataBreach that affected millions of customers and hurt their credibility in the marketplace.
Yesterday, California's A.G. reminded consumers that they have the right to demand their data be deleted and that 23&Me destroy any genetic samples. (I would add that you also have the option of downloading your #DNA data and then uploading it to #GedMatch .)
@geneadons #Geneadons #Genealogy #GeneticGenealogy #23andMe #dnatestingfirmintrouble #DNAtesting #DataPrivacy #DNAdata #DNAdatabases
23andMe’s bankruptcy means that the company will be put up for sale, and there’s no way of knowing who is going to buy it, why they will be interested, and what will become of its millions of customers’ DNA sequences. Read more at @404media. #23andMe #DataPrivacy #CyberSecurity #Tech #Technology https://flip.it/pFwYFl
Good morning and happy Monday!
Sip your morning beverage and go over what #InfoSec and #DataPrivacy news items you may have missed from this past weekend!
Read it here & share to boost someone else's day!
https://open.substack.com/pub/sherpaintelligence/p/whatd-i-miss-the-sherpa-intelligence-c35?r=272cku&utm_campaign=post&utm_medium=web&showWelcomeOnShare=true